This post was made on the 20. 04. 2019, so this information is probably no longer relevant, if you are reading it after that.
Tested as of 22. 10. 2019, issue persists, but to remedy part of the issue, bigger PNGs are now displayed as JPEG, till you click on them.
Tested as of 17. 04. 2021, issue persists.
So a week ago I stumbled upon an interesting find in my Apache logs. A LOT of requests to the same image from the same 2 ISPs, Google and Psychz Networks.
After digging deeper, I noticed that all the images that were getting requests, were linked on Discord.
Note: I’m writing this only due the the fact that I was politely asked to fuck off from the OFFICIAL Discord TESTERS server.
I reported this issue to Discord Support via Email, but got told to fuck off again. Totally ignoring the resizing part.
Disclaimer: I am not in any way, shape, or form responsible for your actions. If the furry gang is kicking in your knees, don’t come crying here. You were warned.
What do you need?
- An Discord Account,
- some common sense.
Step by Step:
0. Find an image and get it’s link (example: https://posili.me/i/gold.png), the bigger the image the better (in our case 24MB),
1. Post the image link to any Discord chat/server,
2. Copy the link to the image (CTRL + SHIFT + I then get the Discord link (images-ext-2.discordapp.net/
3. Edit width and height in the URL, this will for whatever reason re-download the image again and again, as long as you change the values,
4. ???
5. Profit
n. Works with any type of link, just keep adding ? and random garbage on the end.
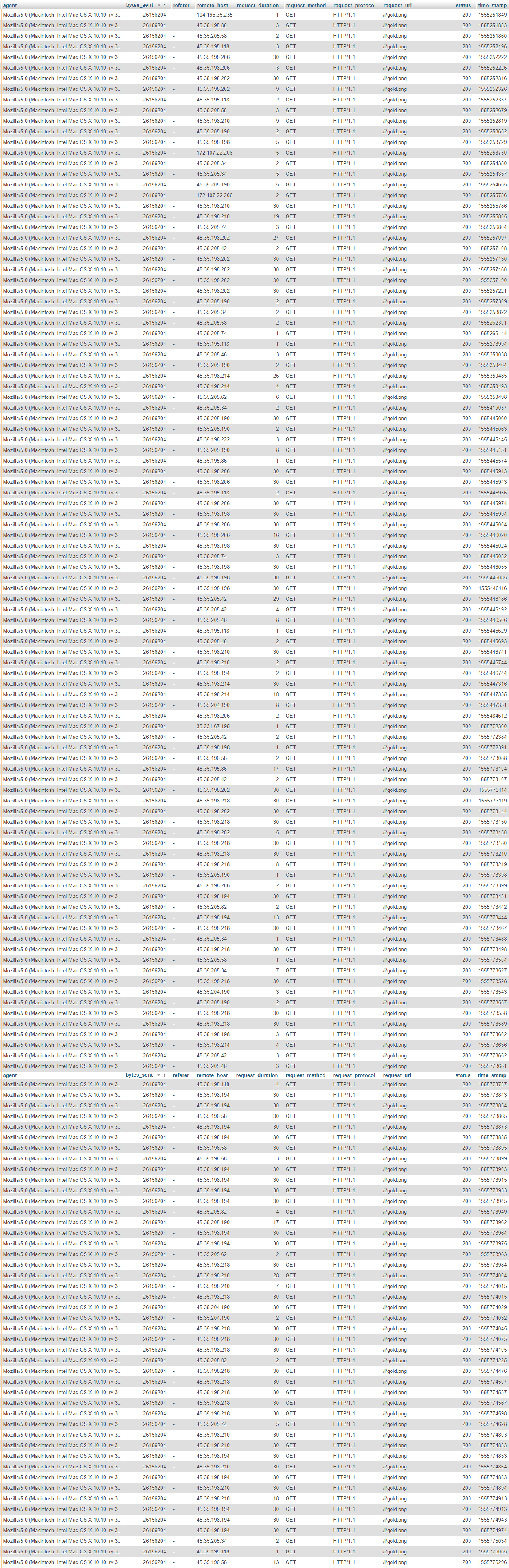
Free DoS from the Discord Testing server, thanks.
That’s It, You’re Done!
You have either killed my poor ScaleWay VPS or Discord patched the problem.
Awso Discowd Team, don’t ban me fow this. *inhales deeply*
